Our Goal in This Challenge
You can reach the challenge from : here
When running the file we can see the application asking for username and passwords. our goal is getting the credentials.
Getting the username
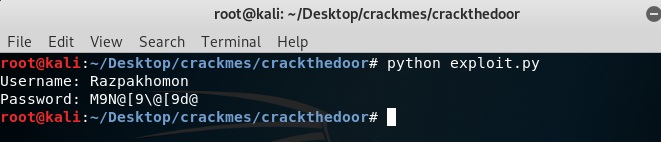
To get the username you do not need to do reverse engineering. When you read the application’s results, you will see the username.
Reviewing with IDA PRO
Now we have to do some hard stuff for finding the password algorithm.
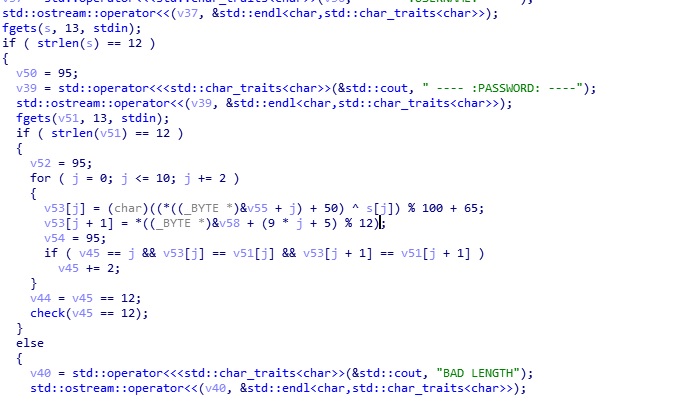
All we need in this photo. first, this checks the username’s length. If its 11 chars, it checks also the password length. if its 11 length to it checks is password true or not. Now we have to understand what it does. now we have to get some values. They are “v53 and v58”. They will be our first_keyword and second_keyword.
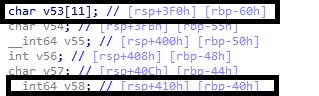
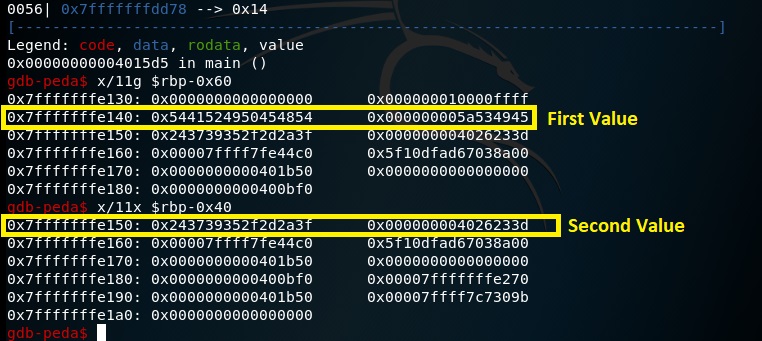
Now we will get that values with using GDB. You can see in the photo.
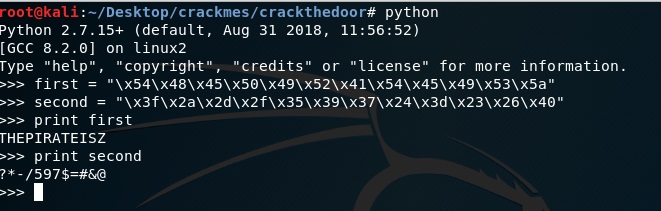
Now we will write these values with Little Endian Format and decode to ASCII from hex. I used python to do it easier. I could use online tools also.
Now we have values and algorithm. Final part is using these values in that password check algorithm.
Here is the algorithm (This same with photo under the title but I converted to this because this is more readable):
tmp1 = ((*(BYTE)(&a + i) + 50) ^ username[i]) % 100 + 65
tmp2 = *(BYTE)(&b + (9*i + 5) % 12)
if (tmp1 == passwd[i] && tmp2 == password[i + 1]){
counter+=2
“&a” = our first value , “&b” = second value ,”&username” = Username that we wrote , “&tmp” = Our flag and “&password” = Password that we wrote.
Final Part
Now I will put values in algorithm. And I will do it with Python Script that I developed.
#/usr/bin/python
first = [0x54, 0x48, 0x45, 0x50, 0x49, 0x52,0x41, 0x54, 0x45, 0x49, 0x53, 0x5a]
second = [0x3f, 0x2a, 0x2d, 0x2f, 0x35, 0x39, 0x37,0x24, 0x3d, 0x23, 0x26, 0x40]
username = "Razpakhomon"
flag = []
for i in range(6):
flag.append(chr(((first[2*i] + 50)^ ord(username[2*i]))%100 + 65))
flag.append(chr(second[(9*2*i+5)%12]))
print "Username: " + usernameprint "Password: "+''.join([str(x) for x in flag])
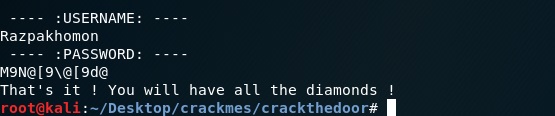
GOT IT
Thanks for reading 🙂

Leave a Reply